Novalys’ Application Security product - Visual Guard was showcased in the Virtual Cybersecurity Tour by Business France North America.
Visual Guard News
Multi-factor Authentication Security for Business Applications
Visual Guard offers a multi-factor authentication solution for your business with low cost, high security & agility features.
RSA Conference 2020 in San Francisco, USA
The Visual Guard team discussed business applications’ security solutions at the RSA Conference 2020.
Visual Guard 2019 is Available
Visual Guard 2019 brings compatibility with .Net Core to secure cross-platform (Windows, macOS, and Linux), Cloud and IoT applications.
It also includes a new module to simplify integration with Angular applications.
COMING SOON: .NET CORE, OAUTH 2, SAML 2.0 AND MORE...
Stay tuned for more innovative features expected with Visual Guard 2019
FIPS Compliance
By connecting to Visual Guard and accessing the Encryption settings you can enable the FIPS compliance mode .
Use/Edit AD Accounts Attributes from VG
Map Active Directory accounts attributes with Visual Guard users attributes to reuse or edit AD accounts and synchronize AD and VG user accounts.
Best practices for Application Log & Audit
Follow these guidelines to improve traceability, monitor sensitive activities in business applications.
GDPR Compliance for Business Applications
This paper summarizes how GDPR applies to the context of business applications and explains how Visual Guard helps to make your applications GDPR compliant.
What is new in VG 2018?
Not only VG2018 is expanding its feature set, it is also addressing GDPR requirements, by helping organizations making their business applications GDPR compliant.
Sending notifications for sensitive events
VG 2018 can send email notifications when certain activities are detected. Alert administrators, controllers or managers when certain events occur.
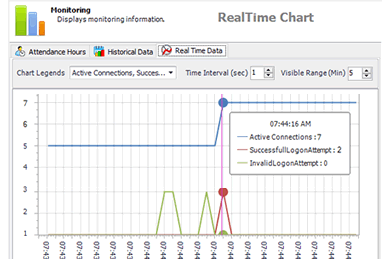
Monitor activities with real-time graphs
Monitor sensitive activities in real-time: access to certain data, execution of certain business transactions, trigger of certain security events, etc.
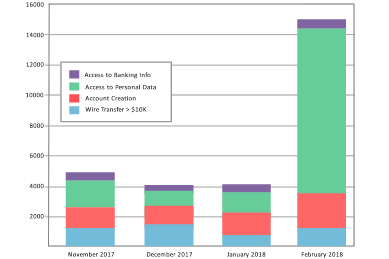
Analyze activities with historical graphs
Generate historical graphs to analyze business trends and detect possible issues.
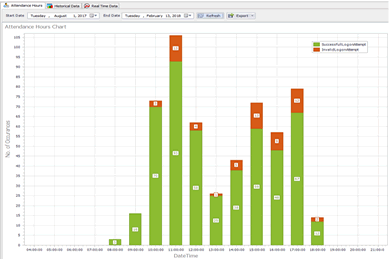
Review application usage with attendance graphs
Visualize the time when the user was or is connected to the application.
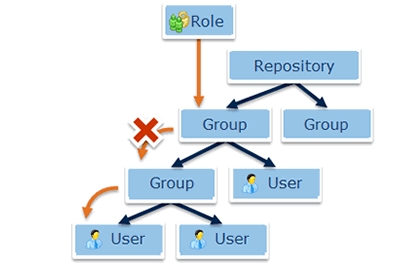
Auditing Permissions in VG 2018
It may be complex to keep track of user permissions therefore, VG 2018 introduces new features to list permissions of a user or a group and find their origin.
Listing the permissions of a particular entity
Get a complete list of permissions, for a given user, group, role or permission set.
Finding the origin of a permission
You may wonder where a particular permission is coming from. Via which permission set(s) and role(s) was it granted?
Federate multiple Active Directory (Domains)
VG 2018 natively supports configurations with multiple Active Directory.
New window for selecting Windows accounts
VG 2018 includes a new search window to query Active Directory and declare Windows accounts or Windows Groups in your VG Repository.
Optional Propagation of roles to sub-groups
With VG 2018, role propagation is optional.
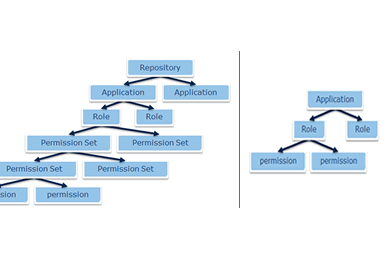
Granting permissions to roles, without using permission sets
VG 2018 introduces an optional simplification: Permission sets are no longer mandatory. If needed, you can directly grant permissions to roles.
Manage large volumes of groups
VG 2018 provides additional features that help managing large numbers of user groups.
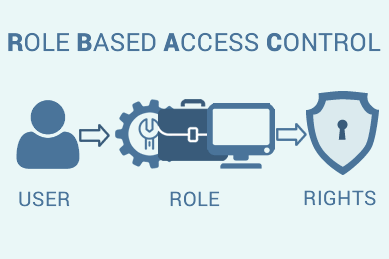
Role Based Access Control for .NET applications
Best practice for authentication and permissions. The objective of this document is to provide the reader with useful information about designing and creating a Role Based Access Control system (RBAC)
Identity and Access Management
How to manage fined-grain permissions in your business applications
This document looks at identity management and access control (IAM) inside applications. It contains recommendations for those in charge of conceiving access control systems, organizing access rights and administering applicative security on the long term.
Protect against security breach
Single Sign-On (SSO) for .NET
What you need to take into account to implement Single Sign-On across your applications.
Access Control for Multi-tenant and SaaS Applications
As with any other application, you may want to secure these applications with user authentication, user permissions and auditing features. In such a case, multitenant applications need to meet several criteria: Protect Data from Other Tenants and Delegate administration privileges...
9 Key Points to Securing your Saas Applications
3 Reasons to "Close All Doors"
Why YOU need to abide by the Principle of Least Privilege.
Most people remember to secure against external threats, but what about the security of internal data in your applications?
Security vs. User Autonomy
How do you balance the access your users need with your company's resources?
The Real Cost of Passwords
How to simplify user management in your applications
Fight Password Fatigue
Password fatigue is the phenomenon of feeling overwhelmed by the need to remember all of them. To combat this, many users have found coping strategies that undermine the security policies that the passwords were created to enforce.
 How to Comply with Security Standards for Health Care Applications
How to Comply with Security Standards for Health Care Applications
Governments around the world are promoting and standardizing the digitization of patient information in the health care sector... Specifically, we will look at how the United States has implemented certain regulations that obligate health care actors to add new features to their applications within a certain time frame; this requires a solution that meets standards across the board and is easy to implement even in existing applications
Securing Your .NET Applications – A Summary Review Of Visual Guard
I think any developer will agree with me that adding security features to an application can be an absolute pain. [...] with Visual Guard from Novalys, the integration of security features is no longer a slog...
 Access Control in Multi-Tenant Applications with Visual Guard
Access Control in Multi-Tenant Applications with Visual Guard
"Multi-tenant" and "Software as a service" applications are becoming more and more common. Companies are looking for different ways to manage their IT needs. They expect solutions that can adapt to their internal organizational structure and lower their deployment and maintenance costs. Multi-tenant applications allow just that – low cost and flexible architecture. However, multi-tenant applications also pose unique challenges. In this article, we will look at security administration and user management in a multi-tenant application with Visual Guard.

For the second year in a row, Visual Guard was chosen “Best Authentication Tool” by the readers of Code Project.
Code Project runs an annual reader survey, asking them to rate their favorite tools, in categories such as Reporting, Debugging, and SQL Database tools. These results, decided by a community of developers more than seven million strong, are based on real trials and in-the-field experience.
Visual Guard is thrilled to be in the company of tools from companies like Red Gate, Intel, and SAP.
See for yourself why Visual Guard was chosen “Best Authentication Tool”

The Real Cost of Passwords
How to simplify user management in your applications
In a 2002 NTA Monitor survey, it was found that the typical intensive computer user had, on average, 21 passwords. ... Password fatigue is the phenomenon of feeling overwhelmed by the need to remember all of them. To combat this, many users have found coping strategies. For example, they often create a list of passwords in a file, or even put them on post-its stuck to their terminals. All of this undermines the security policies that the passwords were created to enforce.
 Visual Guard Recognized for Excellence with
2009 Readers' Choice Award from Visual Studio Magazine
Visual Guard Recognized for Excellence with
2009 Readers' Choice Award from Visual Studio Magazine
"This isn't a popularity contest. A product that earns a VSM Readers' Choice Award has earned the respect and loyalty, over time, of VSM readers, some of the most demanding users on the planet" Michael Desmond, Visual Studio Magazine editor in chief.
 The Code Project announced the winners of their First Annual Members
Choice awards for best development products and tools.
The Code Project announced the winners of their First Annual Members
Choice awards for best development products and tools.
Members were asked to rate their favorites on tools. The Code Project staff then compiled the highest rated listings, awarding the highest ranked in each product category. The results reflect actual perceptions of what developers value. Each codeproject.com member decides which companies or products deserve recognition, based on in-the-field experience.
 Re use Windows Accounts for Applications Access Control with Visual Guard .Net
Re use Windows Accounts for Applications Access Control with Visual Guard .Net
See how to control access to .NET applications reusing Windows accounts for authentication. Integrate with Active Directory and grant roles and permissions to Windows accounts. Define permissions without adding code thanks to .NET reflection mechanism.
 Adding security to an application can be remarkably
easy with Visual Guard for .NET
Adding security to an application can be remarkably
easy with Visual Guard for .NET
Application security is such
a problem that most developers prefer to ignore it. If ignoring
it is impossible then we often implement a custom solution with
user lists and passwords, or we simply expect the user control provided
by the operating system to do the job [...] Visual Guard for .NET
puts an end to this shoddy approach to security by making it trivial
to implement and by providing good administration tools, and it
works for both desktop applications and ASP.NET websites.
by Mike James
 Laboratorio.net - Visual Guard .NET
Laboratorio.net - Visual Guard .NET
El reciente caso aparecido en la
televisión nacional, donde una factura recibida por un usuario
mostraba los apellidos de éste cambiados por palabras ofensivas,
ha puesto en evidencia una vez más la importancia de que las
aplicaciones a través de las cuales los empleados manipulan
los datos con que las empresas operan realicen una correcta autenticación
y registro de actividad de sus usuarios. Este mes presentamos Visual
Guard .NET, un cómodo y útil marco de trabajo que permite
gestionar de una manera eficiente y centralizada los usuarios, roles
y permisos de una aplicación y asegurar el acceso de los usuarios
a cada uno de los elementos de la misma...
by Octavio Hernández
 Secure your Saas applications with Visual Guard
Secure your Saas applications with Visual Guard
Are you creating a security system for a SaaS application? Visual Guard is here to help! This article will list the important questions to ask during your project and the answers that Visual Guard provides to avoid security breaches or functional limitations that will hold you back