Administrators can easily manage users, roles and permissions, while auditors have comprehensive overviews and detailed information to control user rights and sensitive operations in your applications.
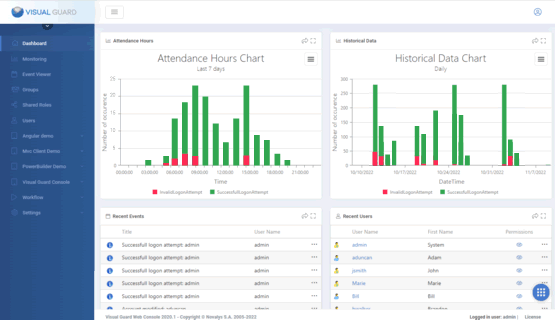
The Dashboard
The WebConsole Dashboard gives access to the main information and features for managing access control.
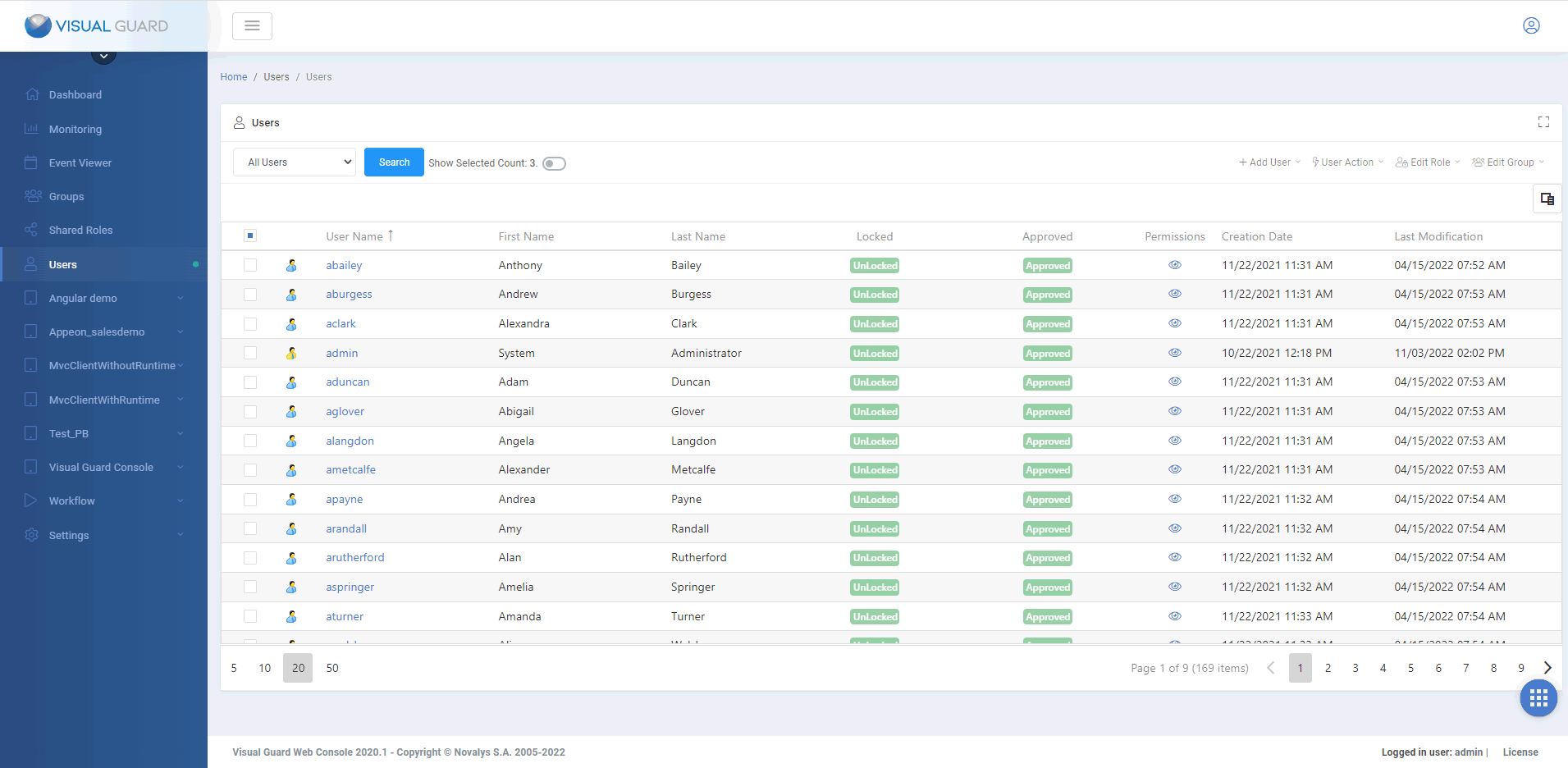
Managing Users
The WebConsole helps administrators manage user accounts.
They can :
- Create, control and manage any type of account (username/password, Active Directory, etc.).
- Manage Groups of Users
- Assign roles and permissions, to users or groups.
- Set up user self-registration, with validation by administrators.
- Set up Multi-factor authentication - for all users or only some of them.
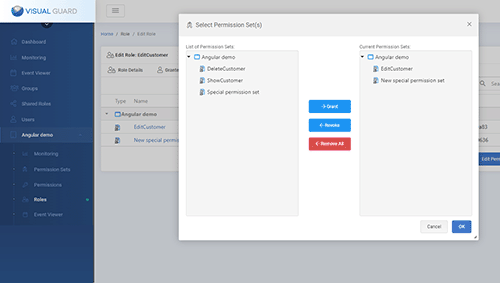
Managing Roles
Administrators can use the WebConsole to group permissions into roles, representing certain functions of your organization.
Two types of roles are available:
- Application roles group permissions enabling features of a single application.
- Shared roles gather permissions related to multiple applications.
Administrators can then assign roles to individual users.
They can also grant them to user groups, in which case all users placed in these groups will automatically be granted these roles.
Administrators can also add user groups below a parent group, thus forming a group hierarchy representing entities of your organization. In this case, children group automatically get the role(s) of their parent group(s).
Finally, in the case of large volumes of permissions, administrators can use the web console to create permission sets, group permissions into permission sets, then group permission sets into roles.
Controlling User Access Rights
The WebConsole helps administrators and auditors to monitor closely the access rights granted to users, which is usually very challenging when users and permissions are numerous and constantly changing:
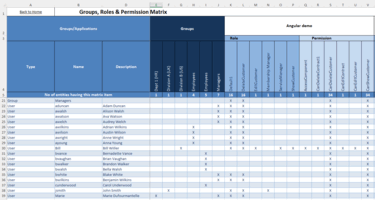
- Generating a permission matrix
The WebConsole can generate an Excel matrix to review the permissions granted to a selection of users, roles, or groups. This matrix will show the permissions and roles granted to each user, as well as the groups they are assigned to. - Detecting inactive user accounts
When users leave the organization or change jobs, they stop using certain applications. In such cases, their access rights should be revoked, and their accounts suspended or deleted, to avoid creating security breaches in the system. The WebConsole can identify such inactive users, using various filters, such as their last connection date. - Auditing user permissions:
The WebConsole lets you review the permissions of a user, and analyze how that permission was granted (from a role given directly to the user, from a role given to the user's group, etc.).
Visual Guard Workflows
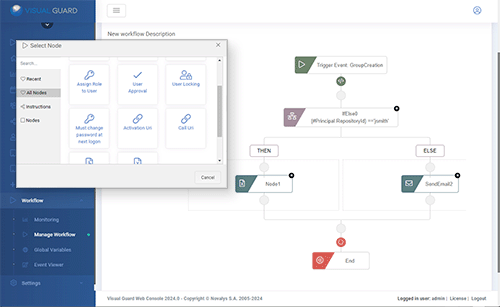
A Visual Guard workflow is a set of automated processes that allow security and identity management tasks to be managed dynamically and efficiently within an application or system.
VG Workflows are designed to automate repetitive processes, reduce human error and accelerate security management operations.
For example, a workflow could be configured for:
- User approval management: Automate the approval process for new users, by defining specific criteria that must be met before a user can access the application.
- Roles and permissions updates: Automate changes to user roles and permissions based on certain events or criteria, ensuring that access rights are always up-to-date.
- Notifications and alerts: Automatically send notifications or alerts to administrators or users based on specific actions or security events, improving responsiveness to sensible events or incidents.
Event Viewer / Audit
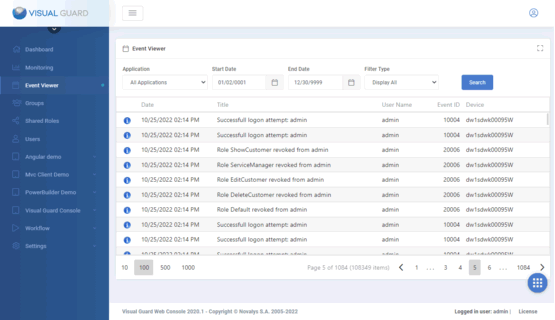
The Event Viewer lets you review security events within applications.
Here are the main categories of events you can find:
- Login Attempts: Successful and failed user login attempts are recorded, along with details of the time, date and user involved.
- Permission Changes: Any changes made to permissions, roles or permission sets are logged, including who made the change and when.
- Administrator operations: Actions carried out by administrators, such as creating new users, modifying roles or deleting permissions, are also logged.
- Security Alerts: Security alerts, such as unauthorized access attempts or modified security configurations, are logged to help identify and respond to potential threats.
To isolate events relevant to an investigation or audit, data can be filtered to specifically target an event type, date range, specific users or critical operations.
The event viewer can be launched from different locations, depending on the scope of the events to be analyzed:
- from a user
- from an application
- at the global level of the Visual Guard repository
Monitoring
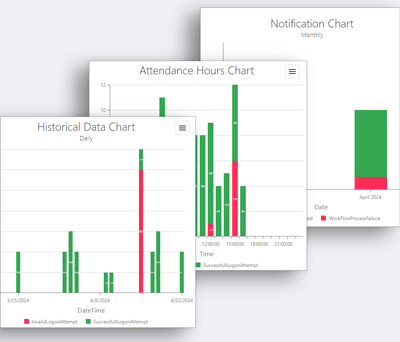
The Monitoring section provides a graphical representation of security events to analyze user activities and system processes:
- Historical graphs
These graphs display data on login attempts, permission modifications and other security events over time, enabling administrators to identify trends or anomalies over extended periods. - Attendance Hours graphs:
These graphs provide a visualization of user connection times to the application. They enable administrators to see when users log on and log off, providing an overview of activity on a daily basis or over specific periods. - Workflow graphs
Workflow graphs show the actions triggered by workflows configured in the WebConsole, including notifications and automated responses, helping to evaluate and optimize response processes.