Traceability & Audit
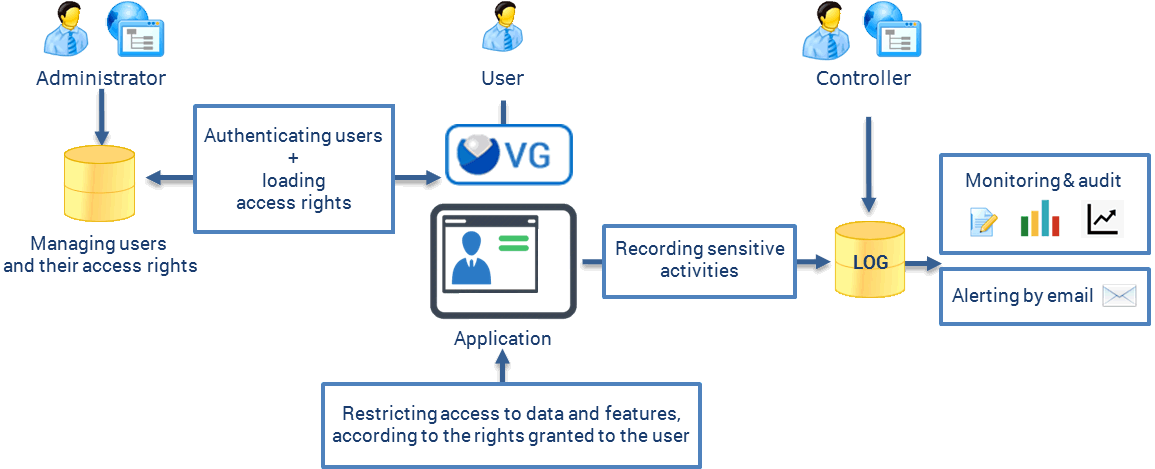
As IT regulations become more prominent for protecting personal, financial and healthcare data, the need for traceability and audit increases.
Visual Guard includes features designed to record sensitive activities, monitor them in real time, send email alerts and audit your applications.
Full coverage
To comply with most regulations and security requirements, these features include:
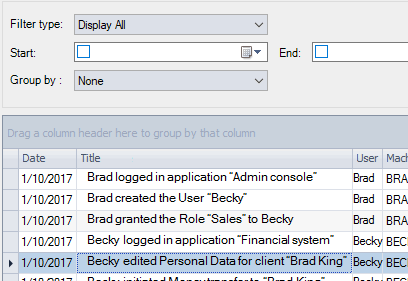
Log important events
Sensitive activities are recorded in a secured Repository:
- Important business transactions
- Access to important data
- Security events (user login, access rights granted…)
- …
Consolidate the trace of all applications in a central location
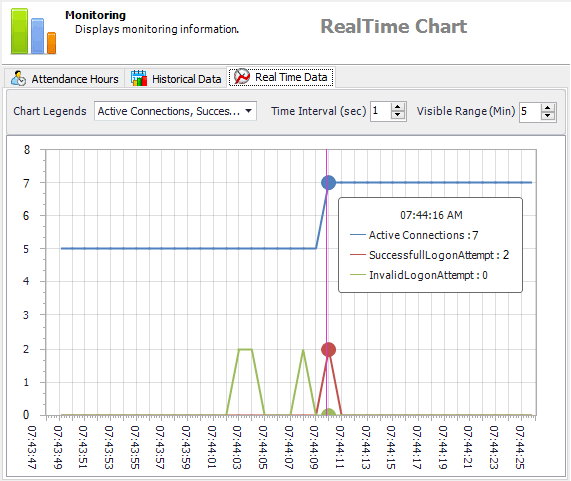
Monitor activities with Real-time Graphs
Monitor sensitive activities in real-time: access to certain data, execution of certain business transactions, trigger of certain security events, etc...
Select certain activities and follow their evolutions - for instance, active connections to your application - or detect possible issues - for example, financial transactions processed at unusual times…
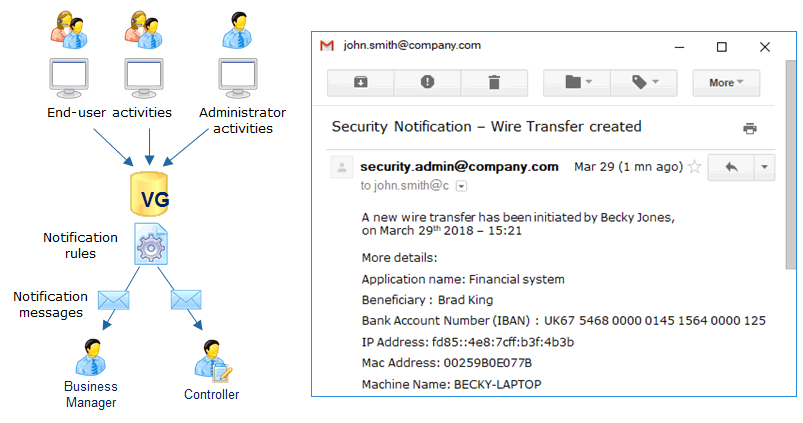
Send email alerts for sensitive events
Send email notifications when certain activities are detected.
Alert administrators, controllers or managers when important or suspicious events occur:
- Business operations (users processing certain data for example)
- Security operations (administrators granting critical authorizations for instance)
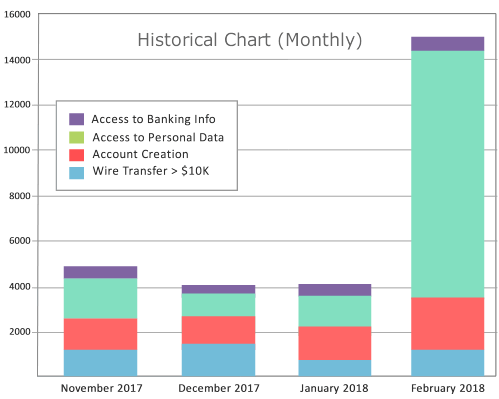
Analyze past activities
Generate historical graphs to:
Analyze business trends.
Detect possible issues - for instance unexpected volumes of operations...
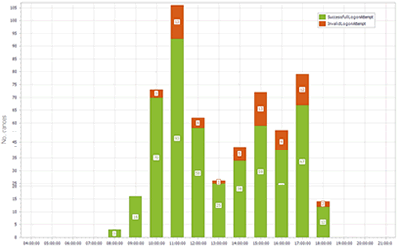
Analyze user attendance
Attendance graphs show you when your application is used.
They display the time and the number of successful or invalid connections.
Audit sensitive activities
Review application security and sensitive activities under various angles:
- Activities of a given user, over a certain period
- Operations performed through a given application
- Activities of a given type (wire transfer for instance) for all users, across all applications
- Certain security events, over a given period.
- Privileged users activities (admins) over a given period, for a given type of event (creating user, granting access rights...).
- etc.
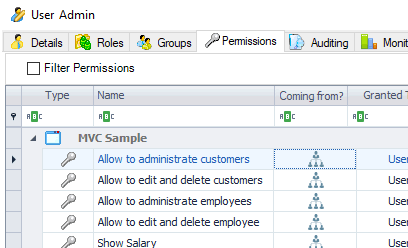
Review the access rights of a particular user
List the permissions of a given user.
The same feature is available to review the permissions of user groups and roles.
Generate reports about your application security
Generate detailed reports.
Document the access control configuration of your application(s) : users, groups, roles permissions, etc.
Independent feature set
Traceability and audit is the 3rd category of features covered by Visual Guard.
If needed, you can implement only audit and traceability features.
Other modules are optional and depend on the requirements you need to comply with (Identity and User Management, Access Control / Fine Grain Permissions).
See also our Best Practices for Logging and Auditing your applications