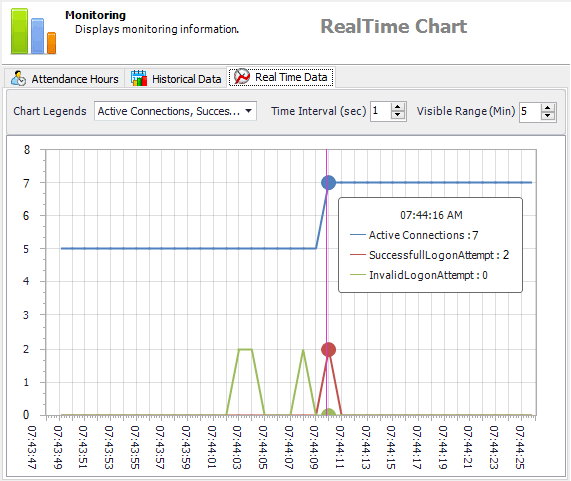
Monitor activities with Real-time Graphs
Monitor sensitive activities in real-time: access to certain data, execution of certain business transactions, trigger of certain security events, etc.
Select certain activities and follow their evolutions - for instance, active connections to your application - or detect possible issues - for example, financial transactions processed at unusual times...