How to comply with security standards for health care applications
Abstract
Governments around the world are promoting and standardizing the digitization of patient information in the health care sector - developers need to find an easy solution to implement these new standards and ensure that this information stays private and secure.
Specifically, we will look at how the United States has implemented certain regulations that obligate health care actors to add new features to their applications within a certain time frame; this requires a solution that meets standards across the board and is easy to implement even in existing applications.
Important features required by these regulations include:
- Securing data
- Auditing features
- Restricting permissions to a need to know basis
- Modularity
Visual Guard is a comprehensive solution for access control in .NET applications from Novalys. It combines authentication, permissions and auditing features in the same tool. A number of Visual Guard clients are public and private health care actors.
This article demonstrates how Visual Guard has been able to help meet the strict criteria of health regulations in the United States. It will look at why two major health care actors have integrated Visual Guard into their applications.
- Introduction
- Background
- Visual Guard in the Health Care Industry
- Protect sensitive data
- Manage Administrative Permissions
- Breaking the development cycle
- Have someone non-technical administer permissions
- Audit Access to Sensitive Data
- Improve Team Efficiency
- Conclusion
Introduction
A system developed for the health care industry needs to be flexible, modular and scalable to meet the security policy of multiple public and private actors. It needs to filter patient information into a need to know basis and protect it from any extraneous forces. A custom in-house access control system can be implemented into a health care application; but, such a solution is usually very complex, time consuming and costly to build, maintain and update. With the strict timelines set by government agencies for the implementation of health care regulations, these deadlines can impose heavy constraints on development and testing time.
"I'm not writing an additional user management system. I'm tired of it." A U.S. State Health Care Department developer now using Visual Guard.
"I'm not writing an additional user management system. I'm tired of it." is something heard often by developers who have gone on to choose Visual Guard as a solution. Visual Guard is an access control system that combines user account management, permissions and audit for one or multiple applications. It is easily integrated into most application architectures (.NET 2.0 and above, C#, vb.net, asp.net, Winforms, WCF, WPF, Silverlight, MVC3, MVC4) and can be implemented in four easy steps (see below) with no need to do a full development cycle each time the application needs to be maintained. Repetitive actions such as administering permissions throughout the application can be done quickly and easily by non-technical employees.
Visual Guard has a number of clients in the health care industry in the United States and Europe, including Federal and State Departments of Health and private actors such as labs and hospitals that specifically chose Visual Guard as their solution because of the flexibility and ease of implementing and using it within their application.
Background
American Health Care Regulations (HIPAA, HITECH, MITA)
There are a number of regulations that need to be met by public and private actors in the health care industry. In this article we will focus on the U.S. Health Insurance Portability and Accountability Act of 1996, (HIPAA). It provides advice and guidelines for patient health data, including its encoding, privacy, security, integrity, and availability. It offers a set of principles to be met by any health care industry actor, public or private, that transmits electronic billing or related information to insurance companies (most notably Medicaid and Medicare) no matter how minimal the services provided are. All the data, processes, and systems throughout the organization are subject to HIPAA guidelines.
Starting in 2015, hospitals and doctors will be subject to financial penalties under Medicare if they are not using electronic health records. Recently, HIPAA guidelines have been additionally reinforced through the Health Information Technology for Economic and Clinical Health Act (HITECH). This is meant to promote and expand the adoption of health information technology. HITECH extends the penalties for HIPAA security breaches to private associates of covered entities and has newly updated civil and criminal penalties to business associates.
There are a number of other standards that regulate applications related to health care data. Both federal and state standards exist. Generally, the most stringent standard, whether it is state or federal supersedes less strict security and privacy standards. For HIPAA, state laws take effect where there are no HIPAA provisions or if there is an exception under HIPAA(1).
Health care application standards are regularly updated to meet with changing technological environments. MITA 3.0 (Medicaid Information Technology Architecture) was recently released. It takes into account enacted legislation such as HITECH, the Children's Health Insurance Program Reauthorization Act (CHIPRA), and the Affordable Care Act (ACA); emerging technologies such as cloud computing are now covered.
A list of regulations from the Centers for Medicare and Medicaid Services can be found here.
Accreditation
Fines are far from the only reason meeting these standards is important. It can take months even years to meet the standards required and get accredited by a recognized institution.
"Losing an accreditation is worse than receiving a fine."
Receiving full accreditation status provides assurance to patients, physicians, payers, health plans, employers and regulatory agencies that an organization's practices are consistent with national standards(2).
Visual Guard in the Health Care Industry
The State Health Department application that Visual Guard secures is a project that ensures citizens are eligible for health care programs and helps them to enroll. It allows citizens to fill in an application, for that information to be verified and to see whether they are eligible or not. The data is then sent on to the appropriate services. It also allows users to renew/update their Medicaid application. The project deadline is set by Medicaid and CHIP (Children's Health Insurance Program).
Another customer, New Century Health, has a provider portal - a custom online portal that provides mainly pre-authorization for oncology treatment requests through various clinical review and approval processes. It is a collaboration platform that is used by physicians, health insurance organizations and employees within NCH.
We will see in the rest of this article how Visual Guard's modularity allows for simple changes to permission and security structures in applications. Visual Guard helps organizations to easily meet changing standards such as securing applications deployed to the cloud.
(1) http://www.managedcaremag.com/archives/0205/0205.hipaabystate.html
(2) http://www.prnewswire.com/news-releases/new-century-health-receives-urac-health-utilization-management-accreditation-132910328.html
Protect sensitive data
HIPAA requires that data be securely guarded. Systems need to:
- "Protect against any reasonably anticipated threats or hazards to the security of such information. This specification is a reasonable and appropriate safeguard in its environment, when analyzed with reference to the likely contribution to protecting the entity's electronic protected health information;"
- "Protect against any reasonably anticipated uses or disclosures of such information that are not permitted or required under subpart E of this part."
Stopping unauthorized access to private data
Visual Guard has created a system that provides safeguards against the most common types of attacks, some examples are:
- ncrypts sensitive data like passwords. A sophisticated Password Policy can be implemented to protect against password cracking
- Protects against DNS attacks.
- Blocks illegally giving supplementary access rights to user accounts.
- Supports SSL/HTTPS protocols and encryption of communications between the browser and the web server...)
- Protects against the capture of data packets to find passwords or security tokens in transit over the network.
- Pre-arms the administration console against SQL injections
- Security data is unreadable by direct SQL access. Visual Guard requires a secured connection via the SaaS application or via the administration interface to read and modify this data.
To read more about Visual Guard security: How Visual Guard protects against security breaches.
Manage Administrative Permissions
HIPAA requires organizations to define what level of access each employee has to the organization's software, based on the role the employee holds within the organization. This is also applied to any third parties that have been given access to the application.
"A physician's primary goal is to give treatment not to remember their passwords" New Century Health Director of Systems Development
For example, someone in the accounting department may require information like address and billing procedures for every client the organization charges. But this person does not need, and should not be able to access patient's case information. Therefore, a system that can define very specific roles and access levels in your software package and that allows customization is needed. This can be tedious to develop, and to maintain. As an access control system, Visual Guard allows for easy management of permission sets. Employees can easily and securely be given, edited or have taken away specific access rights to patient information.
Health care actors need to centralize permissions, as they usually use an in-house application that will be accessed by several entities of a large organization, or various organizations/companies. Such is the case of Visual Guard's client, New Century Health - whose online portal allows insurance companies, doctors and patients to only access pertinent information.
Breaking the development cycle
The majority of projects write application code to define how to apply user permissions. For example, according to the role of the user, this code will deactivate a menu, hide a control, filter a list of data...
As a result, to change the application security (adding new restrictions, for example), there is no need to perform a full development cycle (design, coding, test, deployment).
Visual Guard has developed an innovative technology to eliminate these inconveniences and completely separate security from business logic:
- Visual Guard defines permissions and stores them in its security database.
- When the application is in production, Visual Guard loads the user's permissions from the security database and dynamically applies them. So, there is no security code in the application.
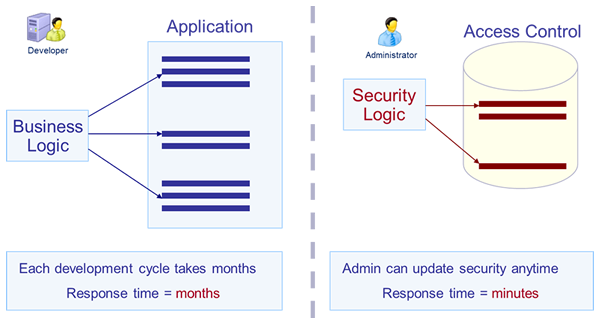
This solution has the following benefits:
- Agility: Update security rules in minutes, even when the application is in production.
- Maintenance costs: No need for changes in the code when security is updated. Avoid a complete development cycle and have a code easier to maintain.
- Implementation: Integration is simple - no need to adapt your application. This technology supports all existing .NET applications.
- Flexibility: This system supports all types of permissions/restrictions in the application.
Each client can be assigned to a group, and their internal structure is replicated through the creation of sub-groups. The same security system is used for all clients, but each client will have administration rights for their users only.
Have someone non-technical administer permissions
Visual Guard allows the giving of privileges to an administrator so that they can manage users and give roles for each application.
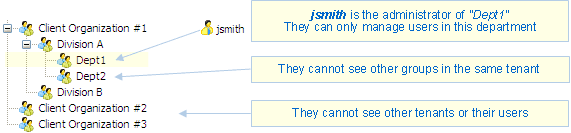
Administration privileges can also be limited to a group of users. In this case, the administrator can only see and manage the users in their group.
When working with a multi-tenant application, it is recommended to name at least one administrator per tenant, and to limit their administration rights to that tenant.
Example 1: you can name an administrator for each tenant
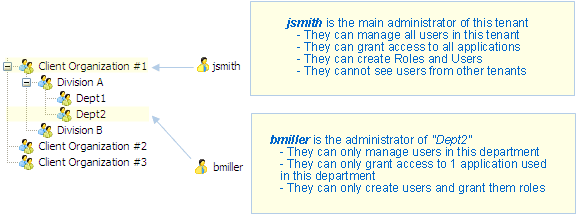
However, Visual Guard can do much more: it can limit administration permissions to any level of the group hierarchy. This system offers a great deal of flexibility for the distribution of administration rights in any entities within each tenant.
Example 2: you can limit administration to a sub-group inside a tenant

Combine multiple criteria to limit administration permissions:
- As shown above, these permissions can be limited to certain groups of users
- These permissions can also be limited to certain applications
- Limit them to certain administration operations (for example, the administrator can create users and give them Roles, but cannot define Roles)
Example 3: you can define several administration levels in each tenant
When your application is being accessed by several entities whether inside the organization or outside, such as insurance companies, it is important to be able to see who has accessed what and to ensure that these rights are not being abused. New Century Health has a portal designed to be accessed by employees, patients and insurance related personnel - each group has access to their specific roles.
Audit Access to Sensitive Data
HIPAA requires that organizations keep an audit log of who did what in the software package. An organization must be able to track when a user accessed each record and if they edited anything within the record. It also specifies that users are only able to access the information that is required for them to do their job.
HITECH requires HIPAA covered entities to report data breaches affecting 500 or more individuals to the Department of Health and Human Services (HHS) and the media, in addition to notifying the affected individuals(3).
As most companies that fall under HIPAA standards are using self-hired external auditors, it is important that they are able to access all the information necessary to ensure that the regulations are being met and that the application is HIPAA certified.
Easily seeing who has accessed what part of a patient's information is therefore essential for any application in the health care sector.
- Generate Access Control Reports: Visual Guard administrators and auditors can generate reports based on the current security data (users, groups, roles, permissions...)
- Logging and Auditing of End-user operations: Save all sensitive operations users have performed in applications secured by Visual Guard. You can then generate reports on these operations (who has done what, when, etc...)
- Logging and Auditing of Administrator operations: Save all operations Visual Guard administrators have performed (create accounts, give permissions, etc...).
Improve Team Efficiency
Simplifying access to administration features
"I think I'm saving 50% of time" New Century Health Director of Systems Development
"I think I'm saving 50% of time" said one of NCH's developers, as with Visual Guard he has reduced such menial tasks like resetting passwords.
The administration interface is as easily deployable as the application itself, enabling one to distribute administration rights in a way that is very flexible. Each administrator is able to access the administration features, no matter where they are or their technical skill.
Visual Guard will provide you with a user administration console in both winform and webform. As an alternative Visual Guard also offers a Custom Administration User Interface:
- A custom ASP.NET or WCF/Silverlight administration interface can be developed and deployed as a separate administration console.
- You can integrate admin control directly into an application. Visual Guard APIs allow all necessary administration operations. These APIs are secured as described above. They allow, in particular, managing the tenants and delegating the administration restrictions to each tenant.
See more information on the APIs here.
(3) http://www.natlawreview.com/article/hipaahitech-enforcement-action-alert
Simplifying user experience by providing Single Sign-On features (SSO)
A user-friendly access control system ensures that the technical team can concentrate on development.
With Visual Guard:
- Users can access multiple applications, passing freely from one to another If the applications make calls to Secured Web Services, the users will also be authenticated for each web service used. Each user will log in to the first site and will then be able to access other sites without having to re-enter their credentials (Single Sign-On).
- Allow a user to authenticate before accessing a website. Visual Guard SSO natively supports multiple types of user accounts (login/password, Windows account...)
- Memorize all or a part of a user's credentials to avoid requiring users to re-enter them on each visit (for example, the username and password)
- Automatically redirects users that navigate between sites federated by the same SSO: the user will immediately arrive at the second site and their security profile is automatically applied
- A section reserved for system administrators allows you to personalize the presentation of the SSO front-end and define certain settings.
Simplifying security implementation - Visual Guard in 4 steps
"Simple, robust, full featured client" NCH Director of Systems Development
The time factor is critical for a number of Visual Guard's clients. They have strict deadlines to put an application into production. The State Department of Health using Visual Guard has less than a year to develop the app and implement the corresponding security.
Integrating Visual Guard is a simple process. Below is an example of how easy it can be to integrate Visual Guard in a .NET application in just 4 steps:
- Adding the Visual Guard runtime to the Visual Studio project of your application.
- Inserting the few lines of code which will identify the user and activate the security.
- Creating a Visual Guard repository and declaring your application through the administration console.
- Generating Visual Guard configuration parameters.
These steps are just an example for a .NET application, as Visual Guard can be integrated into any application that can make HTTP requests.
Conclusion
HIPAA requires that organizations ensure patient data is available to only those who need to see it, including the patients themselves. This availability requirement implies that your system is functional on an ongoing basis and that your data is backed up. It is therefore important to have not only a system that is reliable, but also technical support that is there from inception to implementation of the project.
"Pre-sales and post-sales can be two very different things"..."I had a very uniform experience thanks to Anne" - New Century Health Director of Systems Development
As one of Visual Guard's users mentioned: "it's better to work with a ready-to-use solution as we are not security experts and prefer to focus on our business and core developments, especially when a company has already done the work for us." An all-in-one solution that is very modular and flexible can fit requirements, evolve with the technology and easily adapt to regulations changes or corporate policy updates.
See for yourself how Visual Guard helps meet health care requirements; get a trial version of Visual Guard here.
