GDPR & Business Applications
This article summarizes how GDPR applies to business applications and explains how to make them compliant with Visual Guard ready-to-use security features.
I. What is the impact of gdpr compliant apps on your business?
Since GDPR became effective in May 2018, companies are required to implement mechanisms to protect user data throughout the European Union.
Are you sure you comply with all GDPR requirements?
Are there any aspects that you haven't covered yet?
This article recaps obligations specific to business applications and how Visual Guard facilitates compliance that may otherwise be difficult to achieve especially for existing applications.
1.1 What is GDPR?
The General Data Protection Regulation (GDPR) is a European regulation aiming at protecting personal data for all EU citizens.
Sanctions for non-compliance can go up to 20 million € or 4% of your organization’s annual revenue.
1.2 Does GDPR apply to your application(s)?
Your application(s) should comply with GDPR if:
- Your organization is based in the EU, or
- If your application(s) process data from EU residents.
Note: Application owners are responsible for implementing data protection measures and demonstrating their GDPR compliance, even if the production of their applications is outsourced to another company (for instance a cloud provider, hosting them in production) - see Recital 74.
1.3 Which data is concerned?
Any personal, professional, private or public information, related to an individual (name, address, photo, email, financial details, medical information, blog entry…).
1.4 Is user consent always required?
Not necessarily.
By default, user consent is required, unless processing his personal data is necessary for legal reasons.
For instance:
- The performance of a contract to which the user is a party (employment contract for an employee, commercial contract for a client, etc.).
- Compliance with a legal obligation to which your organization is subject to.
- Protecting the vital interests of the user or another person (for instance, communicating personal data to a third party for safety/rescue reasons).
- The performance of a task carried out in the public interest (police for instance) or the exercise of official authority vested in your organization.
- etc.
1.5 What are your obligations under the GDPR?
Application owners should comply with the following requirements:
- Design: for better protection, you should design and implement data protection measures together with the design and development of your application(s) (Article 25).
See below: "Design data protection and application together" - Data access control: you should implement mechanisms to
ensure that personal data is only processed by authorized personnel, and
only when necessary (Article 25).
This implies:- A secured mechanism should control the identity of personnel accessing data.
- A control mechanism should restrict access to data according to each personnel authorization.
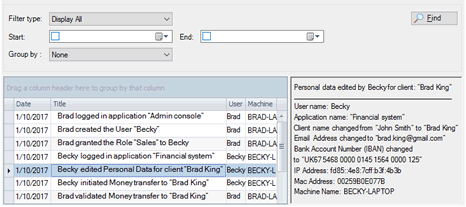
- Log and Audit: you should maintain records of
processing activities for all personal data. These records must be made
available to supervisory authorities on request (Article 30).
See below: "Record and Audit sensitive activities". - Data breaches: in case of a data breach, you are under a legal obligation to notify the Authorities within 72 hours after having become aware of it (Article 33). All the persons impacted by this breach must also be identified and notified (Article 34).
See below: "Detect and Report data breaches." - User consent & access: should you request user consent, it must be explicit (opt-in) and easy to withdraw. You should explain which personal data is processed and how. You should indicate their retention time, and provide contact information to access, modify, erase or transfer their data to another system if they wish to.
II. GDPR and Visual Guard
This chapter explains how Visual Guard will help
make your applications GDPR compliant
2.1 What is Visual Guard?
Visual Guard adds security features inside your applications.
As a result, you can:
- Control the identity of users accessing your applications (Authentication),
- Restrict their access to certain data,
- Keep track, monitor, and audit sensitive activities within your applications
- Send automatic notifications when important events or activities occur.
- Detect and report data breaches
The alternative to Visual Guard is the development of custom security code within each application. More expensive because software developers must reinvent the wheel for each development language used in your organization. Less secured since developers are not security experts, and cannot anticipate all possible issues.
Visual Guard supports all types of application (desktop, web, mobile, SaaS...), all development languages (.Net, PowerBuilder, Angular, Java, PHP…) off-the-shelf. It complies with most security, architectures and network requirements.
2.3 Control Access to your data
Visual Guard controls which personnel are authorized to view or edit sensitive data.
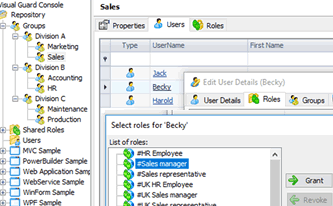
- Authorizations are managed with an administration console, independent from your applications. It does not require any technical skill, and lets you delegate daily security management to the most suitable personnel - for instance, a business manager managing access rights for his team members.
- If needed, you can create new authorizations without touching your code. Pick an application object and select how Visual Guard will change them to enforce the new authorizations. For instance, Visual Guard can hide certain fields, when users cannot view certain data.
As a result, you can patch your security on the fly. If you discover a security breach affecting applications in productions, you can address it immediately, without waiting for the usual dev > test > deployment cycle.
2.4 Record and Audit sensitive activities
2.5 Send notifications when certain activities are detected
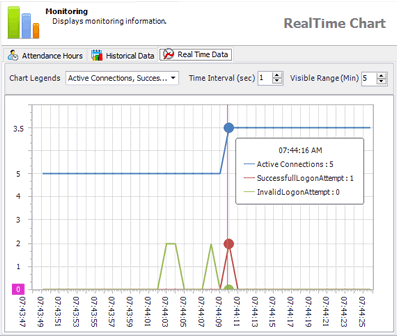
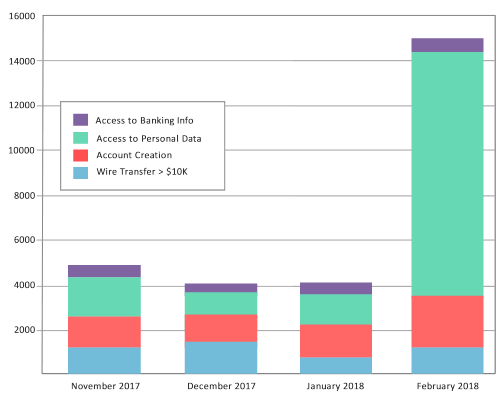
2.6 Monitoring & Reporting
Note: recording and auditing are transversal to all applications:
- Activities from all applications are logged in a central repository.
- No need to review each system separately.
- Controllers get an instant and comprehensive vision of all applications.
2.7 Detect data breaches and report them:
Visual Guard helps detect data breaches:
- Review sensitive activities with real-time and historical graphs.
- Detect suspicious activities - for instance, data processed at unusual times, like nights or weekends, or unusually large amounts of data being accessed. Such activities may reveal data breaches - for example, data being illegally and massively copied.
- Send email alerts to concerned personnel or authorities, to inform them of a possible breach.
- Generate a comprehensive list of data illegally processed, by which user(s), from where, with a list of all the individuals impacted by the data breach.
2.8 Design application and data protection together
When using Visual Guard, the features enforcing data protection are designed and embedded inside your application, to guarantee comprehensive and robust protection.
How does it work?
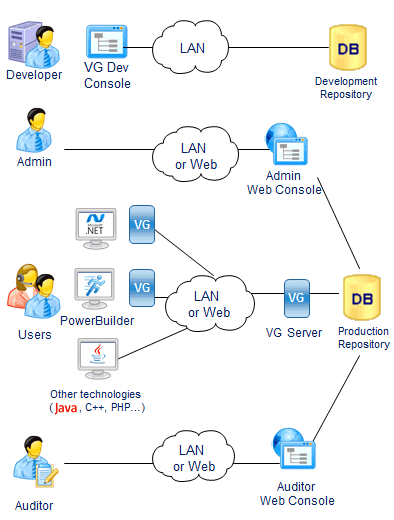
Visual Guard Lifecycle
1. Development
Developers define permissions with the VG Console.
First, permissions are stored in a development repository.
Then, they are deployed in production with the VG Console
2. Administration
Administrators manage Users and Groups,
they grant them Permissions and Roles with a Web Console
3. Enforcement
Users log into the application and VG authenticates them.
Their permissions are loaded from the VG repository,
and applied to enforce Access Control rules.
Sensitive operations are logged in the VG Repository.
Any technology capable of calling web services is supported
4. Audit
Auditors use a web application to review user operations.
They can also control user roles and permissions across all applications.