The Real Cost of Passwords
How to simplify user management in your applications
In a 2002 NTA Monitor survey, it was found that the typical intensive computer user had, on average, 21 passwords. This includes everything from a PIN number on a bank card to a Windows password to their personal e-mail. Password fatigue is the phenomenon of feeling overwhelmed by the need to remember all of them. To combat this, many users have found coping strategies. For example, they often create a list of passwords in a file, or even put them on post-its stuck to their terminals. All of this undermines the security policies that the passwords were created to enforce.
$1 Million a year!
Did you know that a recent Gartner study puts the cost of password management
at between $70 and $200 per user per year? The cost of a lost password
or a security breach is even more expensive! For a company with 5000 employees,
this would mean $1 Million a year just for the passwords!
Bottom line, user management is a very complex and expensive task. User
account provisioning, maintenance and support add up quickly, costing
companies in time and productivity.
This article will propose solutions for developers looking to simplify
user management in two situations:
- Case 1: Single-technology applications (.NET or PowerBuilder supported)
- Case 2: Complex systems geographically distributed and/or based on several technologies
Case 1: Single-technology Applications
A simple thought: what if the easiest solution to manage user accounts is to, in fact, NOT manage them? Why go through all the effort when these accounts already exist in the form of Windows accounts in Active Directory?
Re-using Windows accounts to identify the user of an application is a feature that can be developed for any existing application, although it may require the developer to dive into Windows APIs and fight a bit with low level code…
The other option consists of integrating ready-to-use solutions like Visual Guard, a product that performs authentication and security. Re-using Windows accounts becomes simple, only requiring the addition of a few lines of code in the application (see listing 1).
Get rid of multiple username/password combinations!
As a result, the developer does not have to define, unlock, or
maintain user accounts anymore: the Windows administrator does it for
them!
As for the user, now all they have to remember is their Windows password
to access all applications.
There is even the possibility of implementing Single Sign-On: instead
of asking the user for his Windows password, the application considers
the authentication done when the Windows session was started and automatically
lets the user enter the application!
If you cannot use Active Directory, then a database centralizing all user
account information – independently from all applications –
may be the best solution.
Again, this can be done manually, or with a packaged solution. With Visual
Guard, you can also combine username/passwords accounts and Windows accounts
within the same application – in case only some of the users have
valid Windows accounts.
Finally, the Access Control repository is centralized for all your applications,
which means only one users list must be maintained.
Learn more:
How to integrate Visual Guard in your applications
How to implement Single
Sign-On & reuse Active Directory in .NET Applications here
How to implement Single
Sign-On & reuse Active Directory in PowerBuilder Applications here
Case 2: Complex systems
IT systems that are geographically distributed and/or based on several technologies often come with severe challenges. Let’s review them to find the best solution:
Development Challenges
User Management becomes even more difficult when considering heterogeneous
environments, with applications in many different technologies, including
.NET, PowerBuilder, Java and others.
Developers must balance several requirements:
- Integration of all technologies used within the enterprise
- Elimination of all security breaches to protect from unwanted intrusions
- Construction of a stable authentication system that guarantees permanent access to all applications
- Centralization of user data, even if all production sites are not on the same network and/or cannot directly access the same database
Organizational Challenges
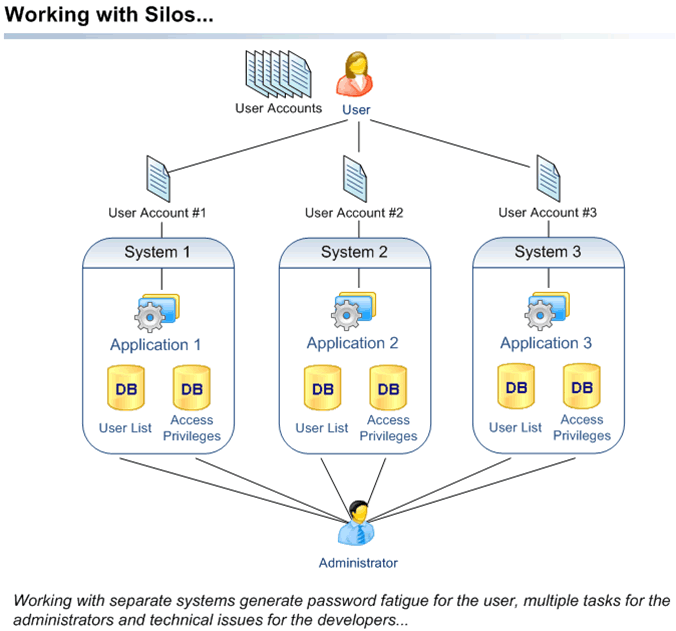
Large companies are often organized into silos – that is to say, systems or groups that rarely interact with each other. For example, in such a company, the finance team would work entirely separately from those in supply chain management. Moreover, companies often have branches or subsidiaries located in different areas. These different locations may use the same system or application. Sometimes these systems are even shared between several distinct societies (for example, supplier/buyer relationships or partnerships). Consolidation of a user list is often advantageous and means significant cost reductions.
However, to make these silos, locations or organizations work together, developers may need to develop connectors or integration systems. The technical work becomes very expensive (multi-million dollar, multi-year projects) and fragile. Updates must be taken into account from all sides of these connections, and this means that maintenance can be very tricky.
Integration of these systems often happens as an afterthought, and therefore security controls are added later. This leads to a reactive posture by the administrators and developers – always playing catch-up with the needs of the users. And the management of any policy becomes very complex, as they are dealing with an existing system, and working their policy around its constraints. Enforcement and audit systems lag behind policy management, or are often completely left out.
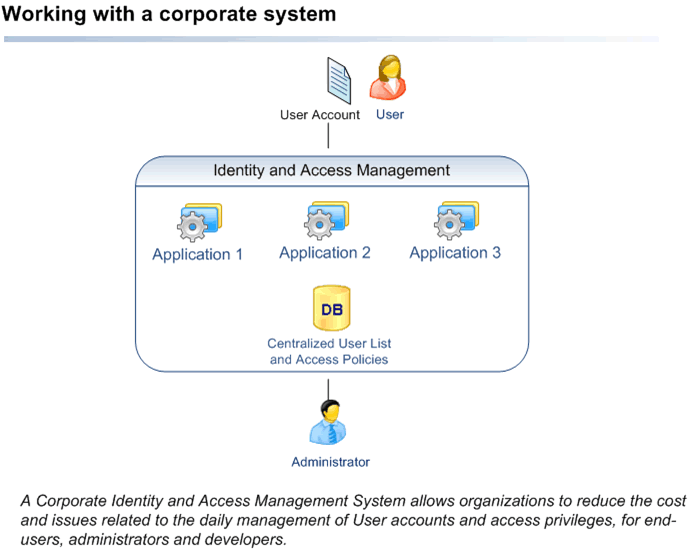
An Ideal Solution
In short, separate authentication systems are not only a headache for developers, but are time-consuming and expensive to maintain. These problems can be solved by a corporate-level solution that centralizes access control administration, enforcement and audit to all applications.
The ideal access control solution should therefore entail:
- A single username/password combination to allow users access to all systems
- Administrators who maintain a single user list across all systems
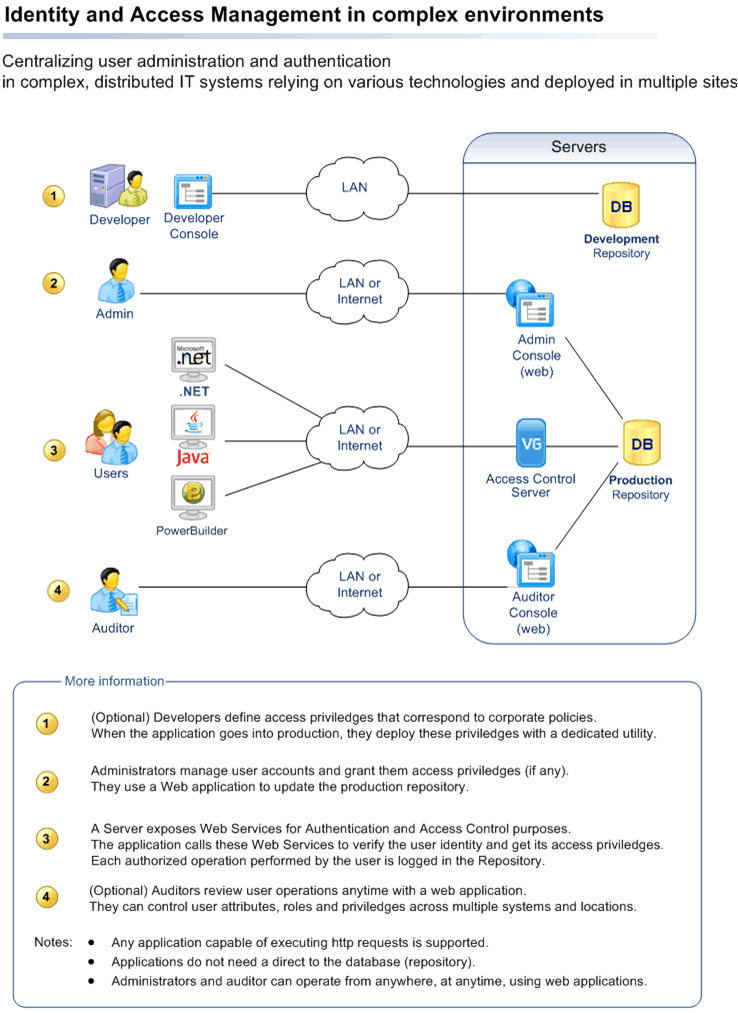
To respond to this, Visual Guard has put in place an access control server, managing a single list of users and access privileges for all applications, no matter the technology, architecture or location.
Visual Guard also features an administrator console to separate the day-to-day administration of users from the technical side. Developers are no longer required to administer user accounts and passwords, so their time is more effectively used. Furthermore, with this Console, no direct connection to the server is required, so administration can be delegated to local administrators who know users best.
Conclusion
Looking at both cases, we can see the advantages of a modular solution such as Visual Guard. It can be scaled to support most architectures and security needs from applications to complex architectures. Because it comes ready-to-use, it requires very little development effort to implement. As a modular solution, it can start small, securing a single application, and grow and evolve over time to secure the entire IT system.
As always, when considering an investment, the cost/benefit ratio must be meticulously examined. For a mature and stable application, management may be somewhat hesitant to invest, wondering if it is worthwhile. However, when the yearly recurring cost of user management can escalate to hundreds of thousands of dollars per year, a packaged solution implemented at a low cost can break even within a few months.