Authentication
The Visual Guard WinConsole offers centralized identity management.
It enables developers to define and apply security policies flexibly across all applications.
Visual Guard supports the following authentication methods:
- Login / Password authentication
- Windows authentication
- Multi-Factor authentication (SMS, emails)
- Token-based authentication (OAuth /Open ID)
- Integration with third-party identity providers
- Single Sign-On based on Windows accounts
- Web Single Sign-On (navigating across websites with a single account)
User Management
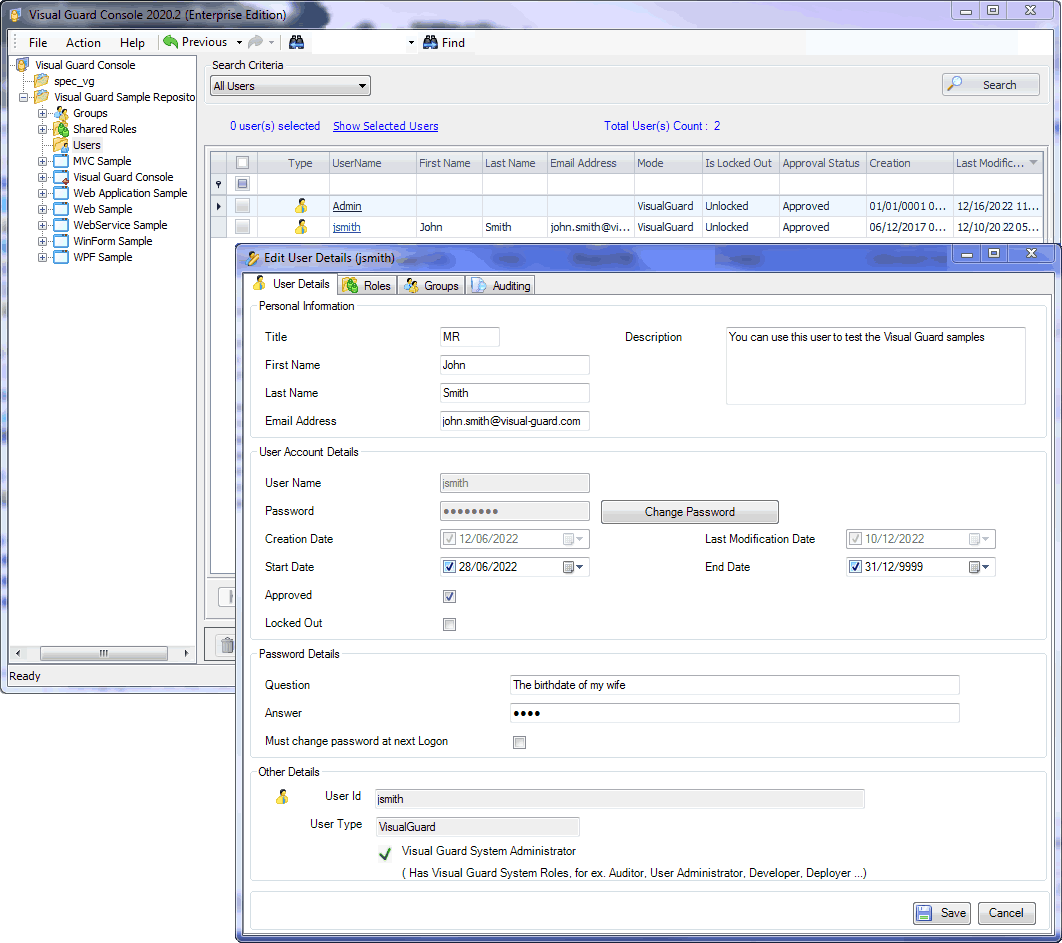
The VG WinConsole features a user management module that can be used by administrators to:
- Manage user accounts.
- Declare Windows Accounts and Windows Groups in the VG Repository,
- Grant Roles and Permissions to users or user Groups.
- Place users in groups
- Define a password policy for Username/Password accounts
Authorizations
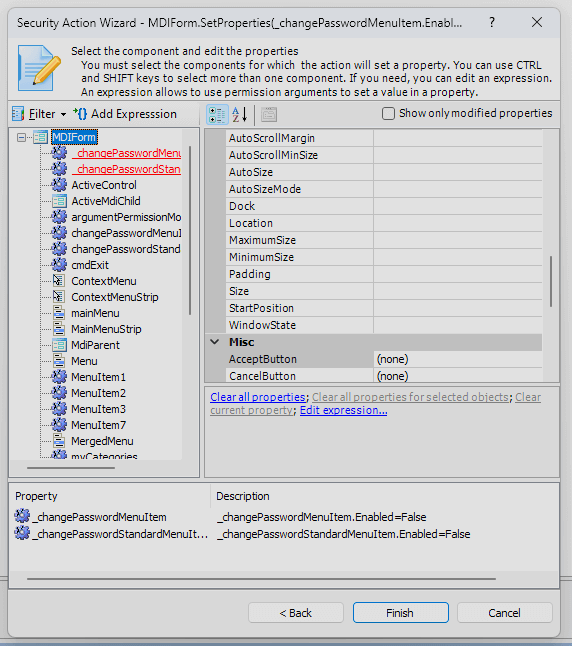
The VG WinConsole allows managing access rights to application features and resources.
In Visual Guard, permissions are hierarchically organized, providing fine-tuned, detailed management of access rights.
Permissions can be assigned directly to users/roles, or grouped into Permission Sets for consistent management.
These Permission Sets can then be assigned to users or groups of users, facilitating the administration of rights according to roles and responsibilities within the organization.
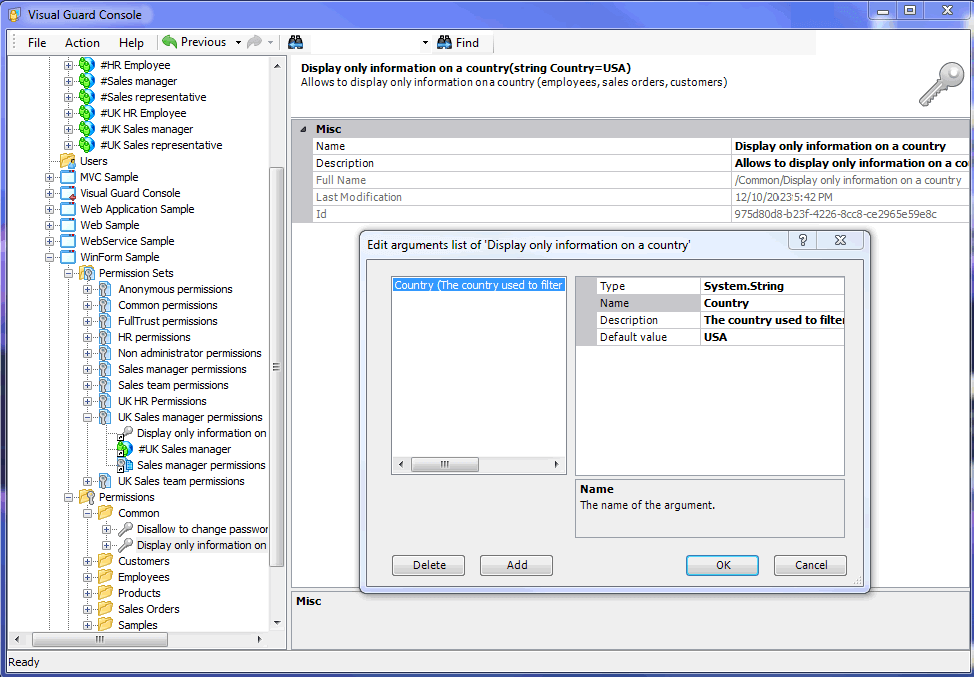
Visual Guard supports both static permissions (hard-coded in the application) and dynamic permissions (context-dependent and applied by VG at runtime).
Dynamic Permissions
The WinConsole allows developers to define dynamic permissions.
These are flexible, context-dependent permissions that adapt in real time to runtime conditions and specific user or situational attributes (role, location, time of day, or any other logical condition).
They are only defined within Visual Guard. Your source code remains unchanged: you don't need to write or maintain security code in your application
Read more about Visual Guard Dynamic Permissions.
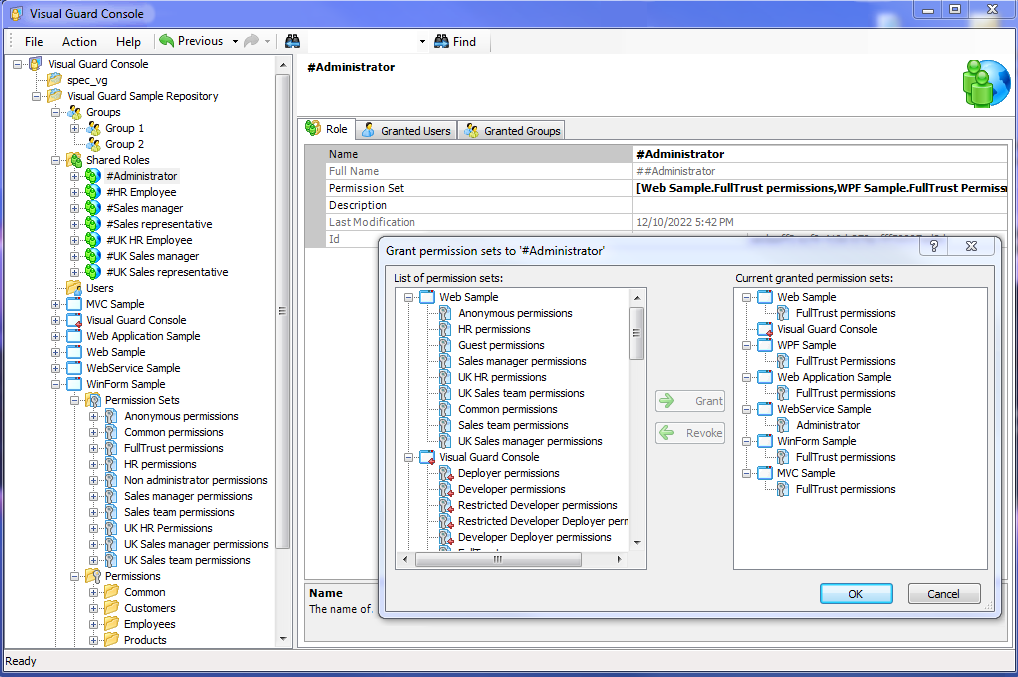
Role Management
Developers or administrators can define Roles, and grant them to users.
Visual Guard provides 2 types of Roles:
1 – Shared Roles contain permissions for several applications.
For example, you may use Shared Roles when your security model includes a limited number of Roles with a large number of applications.
2 – Application Roles contain permissions for only 1 application.
For example, you may use Applications Roles when your security model requires more flexibility and the possibility to grant several roles for several applications to each user.
Each Role will include permissions or permission sets. Once created, they can be assigned to users or user groups.
Security Monitoring, Audit, and Reporting
Auditors can use the WinConsole to review event logs, monitor user roles and authorizations, and ensure compliance with security policies.
This enables them to identify potential vulnerabilities and ensure the integrity of access management within Visual Guard-secured applications.
Real-time monitoring
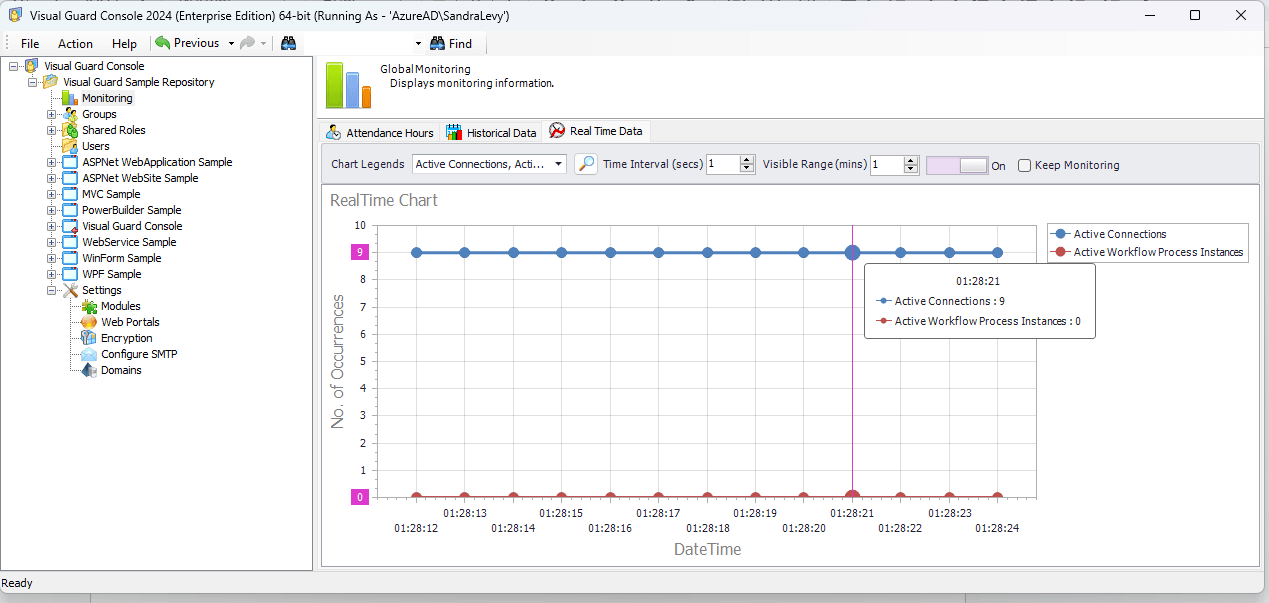
Event Log
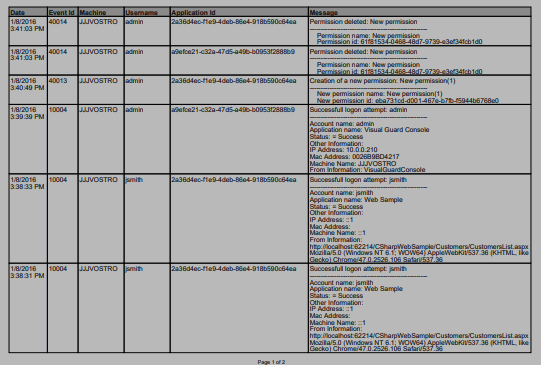
The Event Viewer stores detailed information on various types of security and system events.
This essential feature helps to guarantee reliability and compliance with regulatory standards by keeping detailed logs of all relevant activities within your applications.
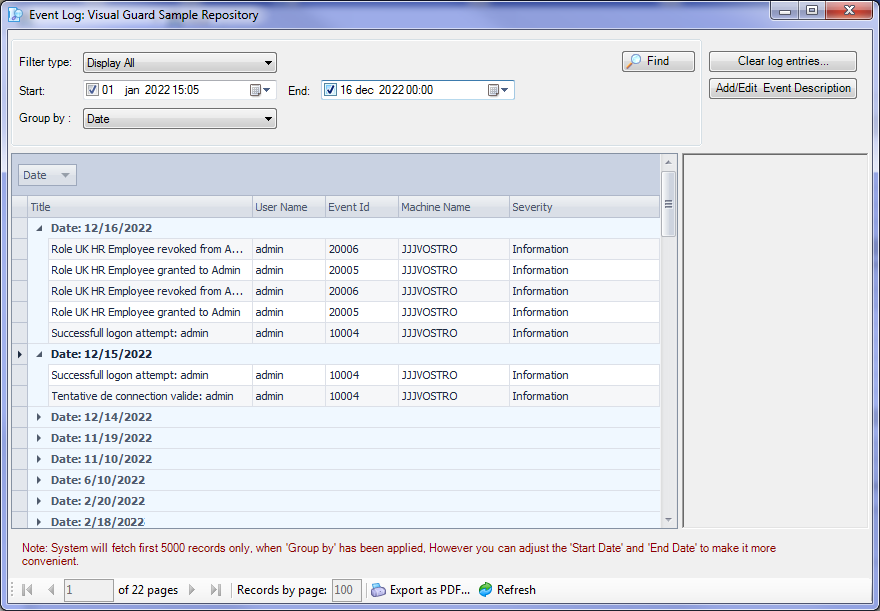
- User activity: details of logins, logouts and other authentication events, so you know who is accessing the application and when.
- System modifications: changes to security settings, configuration and strategy.
- Audit trails: detailed history of actions performed in the system, to track changes made by users or administrators.
- Application Custom Events: events defined by administrators to meet their specific requirements.
- Workflow modifications: automated processes triggered by specific events (sending notifications, blocking or modifying permissions in response to abnormal activity, etc.).
Whenever necessary, auditors can review the activity related to a given type of operation, period or user.
Security documentation
Permission Matrix
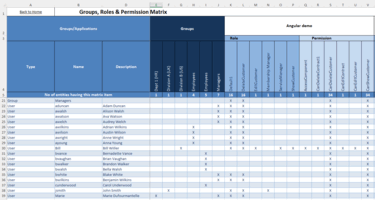
The Permission Matrix provides an overall and detailed view of the permissions assigned to users and groups within an application or application portfolio. It lets you quickly see who has access to what, by displaying a grid where rows represent users or groups and columns represent permissions or permission sets.
This matrix helps to identify granted permissions, detect any redundancies or conflicts, and ensure that security policies are correctly applied to facilitate access rights management and security auditing.
Security report
Auditors can generate documentation on how application security is configured (user accounts, assigned Permissions and Roles, etc.).