9 Key Points to Securing your Saas Applications
Abstract
Are you creating a security system for a SaaS application? This article is here to help! It lists the important questions to ask from the beginning of your project to avoid security breaches or functional limitations that will hold you back later.
- Introduction
- Delegate administration rights to your clients?
- Single Sign-On: simplify the lives of your users
- What if your users could reuse existing accounts?
- Be ready for changes to your business model
- Separate security from business logic
- Pay-per-use Billing and Payment
- Reliability and Performance
- Protection against Security breaches
- Make or buy?
Introduction
The security of a SaaS application should combine both strength and flexibility:
System strength will guarantee application security by:
- Controlling user access within the limits of their subscription
- Assuring data confidentiality between the users sharing the application
- Eliminating security breaches at protecting you from cyber attacks
System flexibility will contribute to the development of your business by:
- Facilitating the evolution of your business model and the creation of your offer
- Responding to client needs related to user management (see below)
- Supporting scalability: optimizing performance and simplifying administration of large numbers of users and secured components
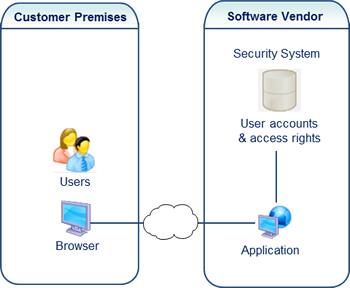
Delegate administration rights to your clients?
Initially, you may be managing users and access rights yourself.
As the volume of users increases, you – and your clients – may wish to delegate certain administration rights so that your clients are managing their users and accounts themselves.
Visual Guard proposes:
- An administration interface accessible to non-technical users, allowing you to delegate user administration to local business managers
- This administration interface includes all commonly required access control functions and offers access via the Internet (account management, assignment of groups and access rights, visibility and control of security data…)
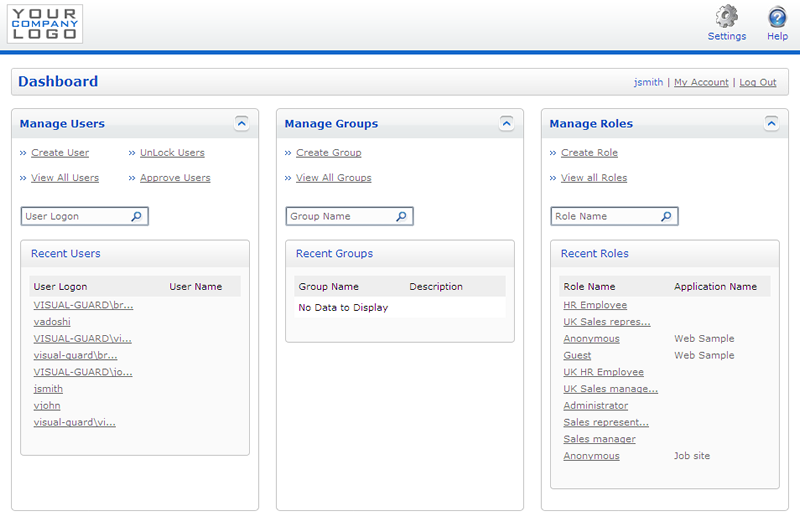
Visual Guard WebConsole Administration Dashboard
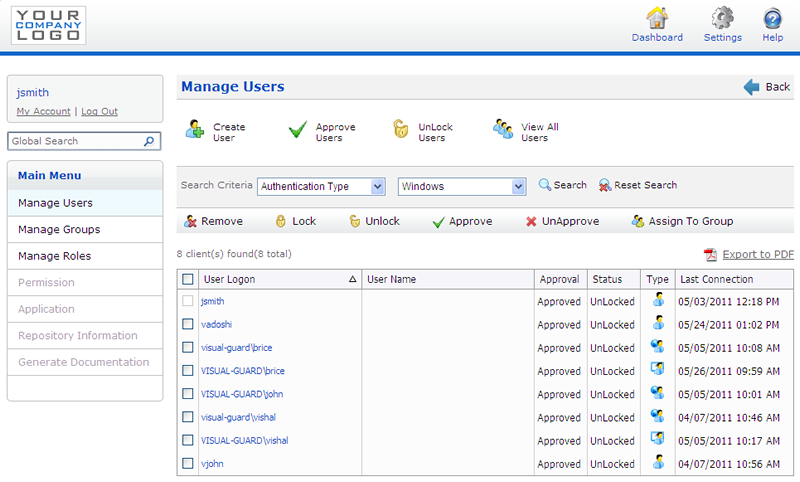
Visual Guard WebConsole User Management
To read more about this administration interface:
If you develop a multi-tenant Saas application (a single instance of the application used by multiple clients), you should restrain client administration rights to their own user accounts: you don’t want them to be able to modify another client’s accounts!
More generally, Visual Guard restricts delegated access rights in three ways:
- Limit user account administration to a client, or a subset of the clients’ users. For example, a sales manager would only be able to define the access rights of their sales team
- Limit the types of administration operations. For example, a business manager would not be able to create new user accounts. They would, however, be able to assign access rights to existing accounts.
- Limit administration to certain application. For example, an HR manager could manage access control to the pay module, but not to the stock management module.
To read more about security for multi-tenant applications:
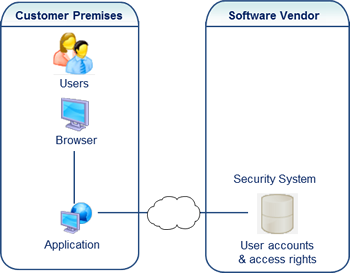
Single Sign-On: simplify the lives of your users
If your product catalogue is composed of a suite of applications, Visual Guard allows you to provide Single Sign-On features (SSO) to simplify your user’s experience:
- They can access multiple applications, passing freely from one to another
- If the applications make calls to Secured Web Services, the users will also be authenticated for each web service used
- Each user will log in to the first site and will then be able to access other sites without having to re-enter their credentials (Single Sign-On)
The Visual Guard SSO system includes the following functionalities:
1 – User session management:
When the user passes from one site to another, the Web SSO system:
- Identifies the user
- Recreates their session for each site visited
- Loads and applies the security data (attributes, roles, permissions…)
Note: The Visual Guard Web SSO includes mechanisms to manage security tokens (to create, transfer and secure the tokens). These mechanisms are optimized to avoid performance issues (for example, it doesn’t “simply” authenticate a user and then reload their security for each page visited: the response times would become too long when the number of visits increases).
2 – Provide a front-end for the Single Sign-On system:
The front-end of the Visual Guard Web SSO:
- Allows a user to authenticate before accessing a website. Visual Guard SSO natively supports multiple types of user accounts (login/password, Windows account…)
- Memorizes all or a part of a user’s credentials to avoid requiring users to re-enter them on each visit (for example, the username and password)
- Automatically redirects users that navigate between sites federated by the same SSO: the user will immediately arrive at the second site and their security profile is automatically applied
- A section reserved for system administrators allows you to personalize the presentation of the SSO front-end and define certain settings.
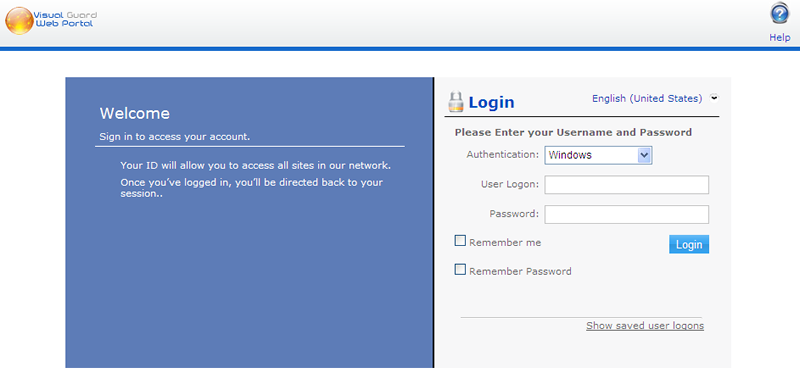
When the user connects to the first site, they will access the login windows where they will choose the type of account and enter their credentials
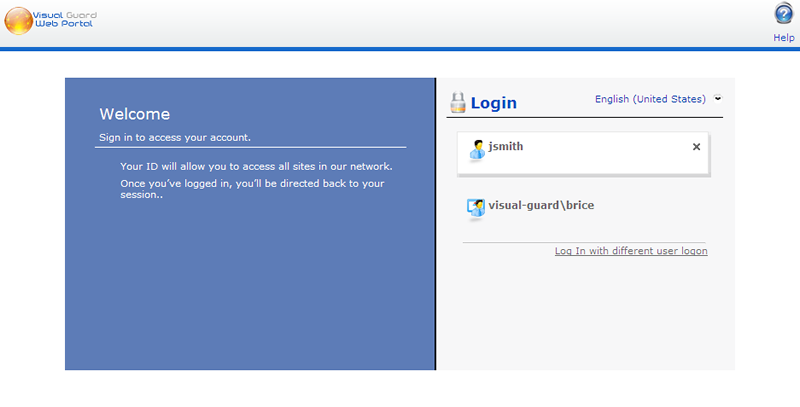
The user can choose to save certain credentials. On their next visit, they can use the account memorized in the system
3 – Facilitate the integration of applications into the SSO system:
- The integration of Visual Guard SSO does not require any changes in the application
- The integration process is the same no matter the type of application and the development technology used
4 – Support for complex configurations:
The Visual Guard Web Single Sign-On supports the following situations:
- Not all sites are on the same network (LAN or WAN)
- Not all user accounts are stored in the same network as the SSO
- Not all sites are under the same web domain
- Not all sites are developed in the same technology
In each case, Visual Guard automatically handles specific constraints. You will find more information on the page Web Single Sign-On (SSO) with the Visual Guard Web Portal
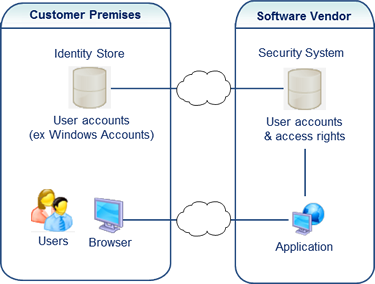
What if your users could reuse existing accounts?
The majority of SaaS applications require that you create a new account for each. The problem is that users already have multiple accounts, which generate significant support costs for companies (see The Real Cost of Passwords).
Certain clients may wish to reuse their existing user accounts (for example, their Windows accounts). Visual Guard allows you to give access rights to your applications to accounts managed by other organizations. Thus, you can federate user accounts from several clients or or partners and define their access rights to your system.
To read more on federating user accounts and managing their access rights:Be ready for changes to your business model
The administration interface must be conceived to manage large numbers of users and access rights (to guide the administrator performing operations and searches, optimize the response time of the security repository…).
When the application is put in to production, the user authentication process and the calculation of their access rights must be optimized to avoid long wait times. For example, a system that needs to access the security repository each time a user opens a new page has a greater chance of performance issues when the number of users and page views increases:
Separate security from business logic
The majority of projects write application code to define how to apply user permissions. For example, according to the role of the user, this code will deactivate a menu, hide a control, filter a list of data…
As a result, if we want to change the application security (adding new restrictions, for example), we need to perform a full development cycle (design, coding, test, deployment).
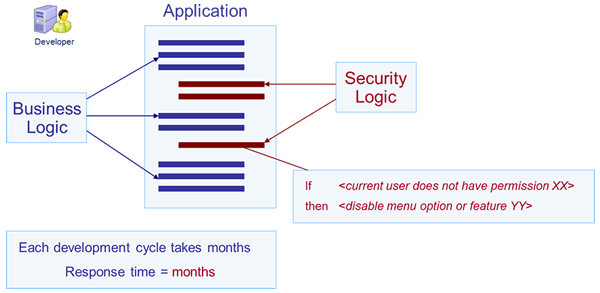
Visual Guard has developed an innovative technology to eliminate these inconveniences and completely separate security from business logic:
- Visual Guard defines permissions and stores them in its security database.
- When the application is in production, Visual Guard loads the user’s permissions from the security database and dynamically applies them. Thus, there is no security code in the application.
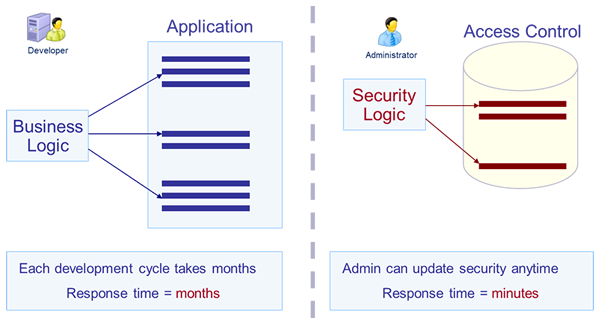
This solution has the following benefits:
- Agility: you can update security rules in minutes, even when the application is in production.
- Maintenance costs: no changes in the code when security is updated. You avoid a complete development cycle and the code is easier to maintain.
- Implementation: integration is simple – you don’t need to adapt yoour application. This technology supports all existing .NET applications.
- Flexibility: this system supports all types of permissions/restrictions in the application.
To read more:
 How to add permissions to an application in production |
 How to integrate Visual Guard in an existing application |
Pay-per-use Billing and Payment
If your business model is based on a pay-per-use SaaS model, or includes temporary use rights, Visual Guard allows you to offer:
- User accounts with a limited time span
- An API enabling collaboration with a billing system to automatically update the expiry date of each account
- A user interface that allows the sales team or helpdesk to modify this information – for example, the treatment of unique cases or errors, taken immediately into effect for the user.
Read more:
Reliability and Performance
Visual Guard’s administration interface has been designed to easily manage large numbers of users and access rights (guides an administrator performing operations and searches, optimizes the response time of the security repository…).
When a SaaS application is in production, the Visual Guard processes that authenticate the user and calculate their access rights is optimized to avoid long wait times (the system does not need to access the security repository each time a user opens a new page, and so avoids performance issues when the number of users and page views increases).
Protection against Security breaches
Since a SaaS application is accessible via the internet and manages client data, Visual Guard has created a system that is not vulnerable to the most common types of attacks:
Unauthorized access to security data:
- Security data is not readable by direct SQL access. Visual Guard requires a secured connection via the SaaS application or via the administration interface to read and modify this data.
- Sensitive data like passwords is encrypted.
Denial-of-service: Visual Guard includes protection against attempts to make it unavailable to customers by saturating it with numerous logon requests.
Unauthorized administration operations: a user could discover how to access the administration interface or the APIs that manage access control. Visual Guard blocks illegally giving supplementary access rights to user accounts.
Interception of confidential information:
- Between the client browser and the web server: Visual Guard supports SSL/HTTPS protocols and encryption of communications between the browser and the web server…)
- Between the .NET components inside the SaaS application: Visual Guard relies on the Microsoft Proxy System (Marshall) to manage and protect such communications
Password cracking: Visual Guard allows you to define a sophisticated Password Policy to protect against password cracking (guessing a password via trial and error).
Packet sniffing: Visual Guard includes a protection against the capture of data packets to find passwords or security tokens in transit over the network. A hacker could steal these tokens to make calls to the system as though they were a legitimate user.
SQL injection: The Visual Guard Administration console contains search fields – for example, to find a user account. It is pre-armed against SQL injections, which consist of inserting parts of SQL statements in the search field, with the goal of consulting confidential information, or illegally changing the security data.
To read more about Visual Guard security:Make or buy?
Timeframe is key: we’ve seen in this article that security and access control for SaaS applications involve complex functionalities. For an internal project, they require a significant time commitment and skilled developers.
If you are working in a limited timeframe or the required expertise is not available, a ready-to-use access control solution like Visual Guard is your best solution.
Risk management: Visual Guard limits short-term risks (cost and time overruns, bugs and security breaches), while providing for other long-term challenges:
- Evolution: consult the history and past versions of the solution: Visual Guard follows technical evolutions of the market; new versions are published regularly.
- Product and support quality: Visual Guard a stable and well-deployed solution, for which you can consult the reviews of other users.
- Longevity: Visual Guard proposes an escrow agreement (a copy of the source code is deposited with a third party who will send it to clients if there is an interruption in service by the provider, Novalys)
Why not combine all these advantages? The Visual Guard team is attentive to their users’ needs when choosing how to continually evolve their application with the market. You benefit from the advantages of a standard solution (more stable and complete at a lower cost) while being able to influence future development to better cover your specific needs.