Make Applications
GDPR Compliant
- Control Access to Sensitive Data
- Track and Audit Sensitive activities
- Detect and report data leaks
- Implement Multi-Factor Authentication
Learn More
What is GDPR
The General Data Protection Regulation (GDPR) became effective on May 25, 2018 to protect personal data for all individuals within the EU.
Sanctions for non-compliance can go up to 20 million € or 4% of organization's annual revenue.
Which data is concerned?
Any personal, professional, private or public information, related to an individual:
Name, address, photo, email, financial details, medical information…
GDPR applies to your applications
- If your organization is based in the European Union
- - OR -
- If your application(s) process data from EU residents.
What are your obligations under the GDPR
- Data access control: implement mechanisms to ensure that personal data is only processed by authorized personnel, and only when necessary.
- Log and Audit: maintain records of processing activities for all personal data. These records must be made available to supervisory authorities on request.
- Data breaches: Each person impacted must be identified and notified. Authorities must also be notified within 72 hours after discovery of a data leak.
- User consent & access: it must be explicit and easy to withdraw. Indicate which and how personal data is processed, its retention time, and provide contact information to access, modify, erase or transfer data.
- Design: implement data protection measures together with the design and development phase of the application.
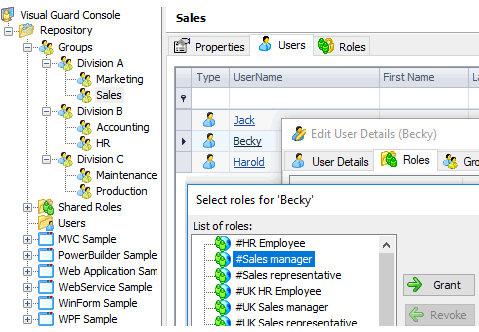
Control access to sensitive data
Visual Guard controls which personnel is authorized to view or edit sensitive data:
- Authorizations are independent from one data to another. They control which personnel can access a data and the type of activities allowed.
- Authorizations can relate to several applications, no matter their respective development languages.
Define consistent and simultaneous authorizations across all applications.
- Authorizations are managed with an administration console that does not require any technical skill.
Entrust daily security management to the best personnel - for instance a business manager.
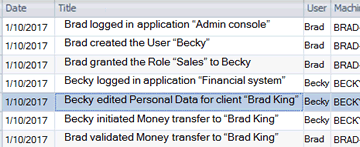
Record and Audit important activities
Visual Guard keeps track of important activities - access to sensitive data, changes of user authorizations, etc.
You can audit users (history of activities, list of authorizations) or your applications (who did what)
- Record activities processing personal, banking or any other sensitive data. Keep track of administrator operations managing personnel accounts and their authorizations.
- Audit and filter sensitive activities with various criteria: for instance, you can review the past activities of a given personnel and his current authorizations - check which data have been processed within given application, when? by whom?
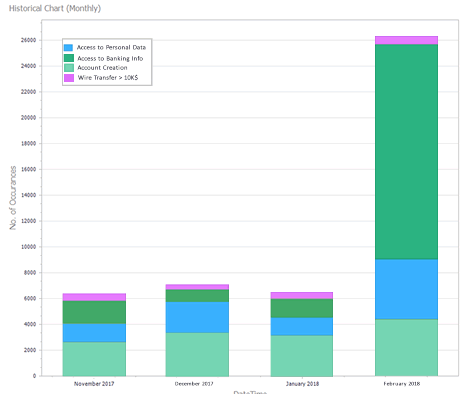
Detect and Report data breaches
Visual Guard monitors accesses to sensitive data, and help detecting data breaches:
- Review real-time and historical graphs about sensitive activities.
- Detect suspicious activities - for instance data processed at unusual times, like nights or weekends, or unusually large amounts of data being accessed. Such activities may reveal data breaches - for example data being illegally and massively copied.
- Send email alerts to concerned personnel or authorities, to inform them of a possible breach.
- Generate reports detailing which data were illegally processed, by which user, from where, with a list of all the persons impacted by the data breach.
Strong Authentication
Visual Guard offers strong, multi-factors authentication mechanisms, to ensure that users are who they claim to be.
For systems with high-security requirements, passwords do not provide sufficient protection.
For example, before accessing a secured application, users must fill a login form, receive a notification on their mobile, and validate it with a pin code or fingerprint.